On a daily basis when paying online or logging into a site, customers and users are completing 2 factor authentication processes without even realizing it. In this article we’ll explain what a two factor authentication system is, when one should be implemented and what the benefits are of having one in place.

You may have noticed that when you are logging into some specific sites you are asked to supply more than just a password. You may need to supply a code sent to your email or mobile phone to be granted access. While this process may seem like a hassle at the time, the admin of that site in fact have your best interests at heart. The process you are undertaking is protecting your personal and financial details from the online world.
In today’s online society, two factor authentication systems are becoming increasingly popular. With a rise in online security breaches where individuals or groups gain access to personal or financial details, having an additional layer of security that only the ‘real’ user should have access to limits detrimental information landing in the wrong hands.
What is a 2 Factor Authentication System?
In short, a two factor authentication system is an additional layer of security for an online website. A user must enter their standard login details such as a username and password along with the second security token to be granted access.
Two factor authentication, often abbreviated as ‘2FA‘ is a system put in place to prevent online account hacking. When a 2FA or multi factor authentication system is in place on a website, more than just a password and username is required when logging in.
It is the third (required after the username and password has been entered) and vital piece of information that prevents hackers gaining access to potentially detrimental information. The third piece of information required by the user is generally something that only they would have access to. This can be in the form of a code sent to their mobile phone via message or it could be a code sent to the users email account.
Two factor authentication systems not only prevent hackers from accessing personal and financial data online, but they also deter people from attempting spam combinations that can potentially slow down a website.
2FA’s combine two of the three authentication systems to provide a stronger login. To be classed as a two factor authentication system, it must require two out of the three authentications below:
- Something that the ‘real’ user knows – for example a basic password
- Something that the ‘real’ user owns – for example a mobile phone
- Something that the ‘real’ user has – for example their fingerprint
When speaking of online logins, a 2FA will be generally comprised of the first and second authentication systems.
 Why is a Password No Longer Strong Enough Online?
Around the world, millions upon millions of people use the internet each day. While the majority of these users are going about their business with no risk to others, a handful of these people aim to hack accounts that will lead them to some financial gain. Viruses and malicious coding can be inserted into a site to constantly collect data entries without the site owner even realizing. This means that a hacker can obtain the credentials for multiple account at once.
While some of us may believe our passwords are ‘strong’ enough, we often reveal many details about ourselves on social media accounts that can hint to our passwords. A 2FA system means that even if a password is compromised the personal account details remain safe.
Why Do People Attempt to Hack an Account?
There are a number of reasons why someone intentionally hacks an account or website.
The majority of the time online hackers intend on accessing a site or account to lead to a financial gain. Other reasons an account may be hacked by someone is so that they can leak detrimental information about a public figure, assume a personal identity or vandalize a website.
A basic account that requires a username and password can be hacked when:
- An attacker guessing a password that is weak or relates directly to the user
- An automated script is used to try different log ins
- The attacker uses multiple sources such as social media to build up a profile about the user and in turn ‘guess’ their password
- Fake pages are set up to draw in users to use the same password they have used for other sites
What Types of Two Factor Authentication Systems are Available?
The type of website you are running and the information you have stored for each user will determine which 2FA is the right fit. While all two factor authentications add an additional step to the login process, they ultimately ensure the security of each member’s account.
1. Email Code
A code that is automatically sent to the users email address. They will then need to login to their email and copy and paste this code into the required field.
If you are using the WP eMember Plugin and intend on implementing an email 2FA system take a look at the Two-Factor Authentication Addon.
2. SMS Code
A code is sent to the user’s mobile phone via text message. This is one of the most efficient 2FA’s as it is almost certain the person with the device is the ‘real’ user logging into the site. It would be almost impossible for a hacker to get their hands on a user’s mobile phone and know their username and password.
While this is a popular 2FA method, it is important to note that this system is only at good as the network. If the person’s phone network does not meet expectations they may never receive the code needed to log into the site.
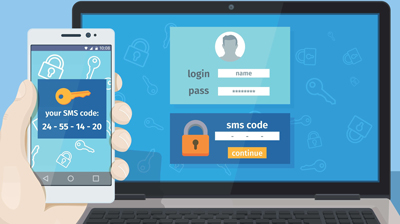
Basic Overview of a Two Factor Authentication Process
You now understand what a 2FA system is although you are skeptical about the steps involved for your customers to login to the site when one is in place. Below we’ve briefly outlined the steps involved when logging into a site protected by a two factor authentication process:
- As a user you land on the login page of the site.
- You enter your basic username and password.
- An automated code will be sent to your mobile phone (or email).
- You will be prompted to enter the code that you were sent.
- If the correct security code is entered you’ll gain access to your account.
To set up a two factor authentication system on a growing website you’ll need to work out what details you have already collected about your users. For example, if you have all your users phone numbers you may be able to implement a system where a message will be sent to their phone, whereas if you have only collected their email addresses you may need to find a 2 factor authentication system that sends a security code directly to a user’s email.
When Should a 2 Factor Authentication System be Implemented?
We recommend that a two factor authentication system should be in place for any site that contains personal or financial details about a user. It is important that site owners have multiple security measures in place to protect their users details.
What are the Benefits of a 2FA and How Do they Create a Secure Login System?
A study found that almost 80% of people use the same password across a number of secure and insecure websites. If a hacker was to get their hands on a users basic login credentials they would have access to not only personal information but more than likely financial assets as well. While the hacker is delving deep into your personal information, no double check has been put in place to confirm they are the ‘real’ user.
When a 2FA is in place, it is a lot harder (and a lot more work) for a hacker to gain access to the account. The user must provide two different pieces of evidence to confirm their login.
2 Factor Authentication Systems:
- Lower the number of successful account hacks
- Deter hackers from trialing multiple username and password combinations
- Ensure that the person logging in is really who they say they are
- Add an additional layer of security especially for those users who have basic passwords
- Provide additional protection against identity thefts
- Give peace of mind to the users that their account is safe
2FA’s Add Security to Admin Accounts
While the majority of the talk has been about the user’s account, two step or two factor authentication systems can be put in place for an admin login. While employees of an organization should be creating strong passwords and usernames, there will always be a handful that go against the rules. Having a 2FA prevents an employee/admin account being compromised. A compromised admin account can be detrimental for a company and ultimately lead to it’s downfall.
Leave a Reply